cPFence gives you powerful options to block malicious or anonymous traffic—including traffic coming from Tor (The Onion Router) exit nodes. While Tor is often used for privacy, it’s also a common vector for DDoS, hacking, phishing, and other unwanted activities. Blocking Tor exit nodes helps protect your servers from anonymous attacks.
Block Tor Exit Nodes Using the cPFence WebUI
The cPFence WebUI makes it easy to block entire countries or anonymous networks like Tor, either for a specific server or your entire cluster:
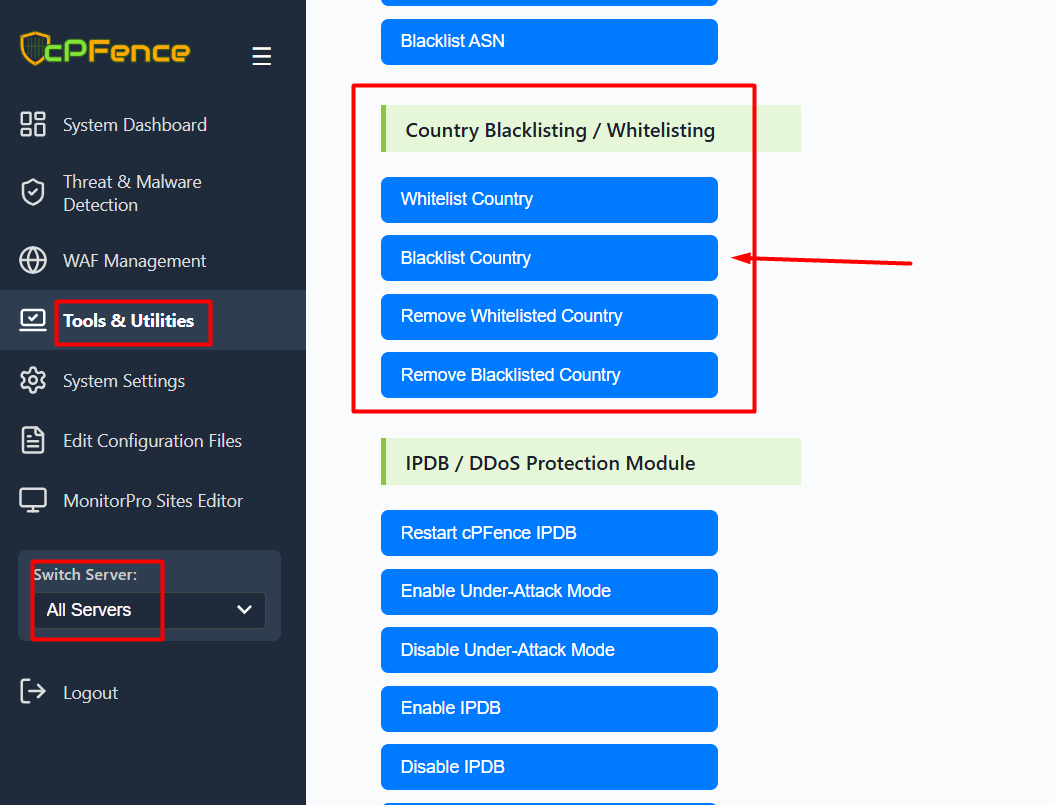
- Navigate to Tools & Utilities in the sidebar.
- Choose your target servers using the Switch Server dropdown (single server or all servers).
- Click Blacklist Country under Country Blacklisting / Whitelisting.
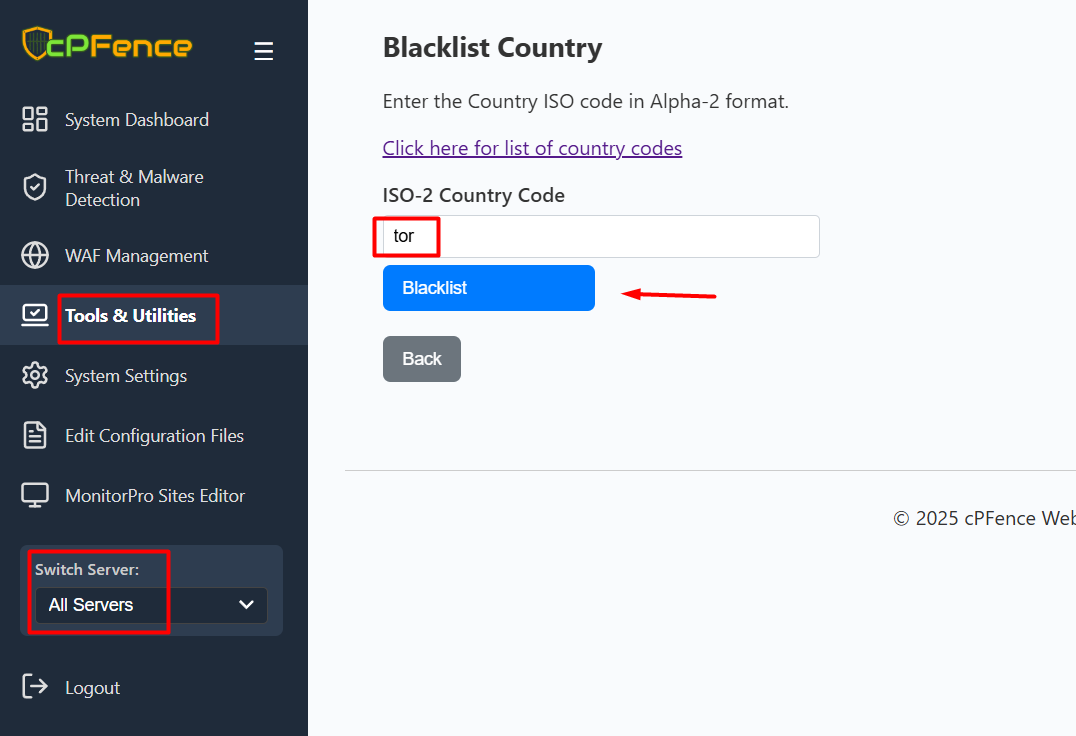
- Enter
torin the ISO-2 Country Code field and click Blacklist.
This will block all Tor exit node IPs automatically—no need to manage large IP lists or custom firewall rules.
Tip: Please use the Blacklist/Whitelist Countries feature judiciously. Limiting this setting to 2 or 3 countries is recommended, as applying it to a large number of countries may negatively impact system performance.
Block Tor via CLI
You can also block Tor traffic directly from the command line:
cpfence --blacklist-country torThis will instantly blacklist all known Tor exit nodes on the selected server.
Additional Notes
- You can whitelist or remove a country/region/Tor network at any time from the same menu.
- Country blacklisting can be applied to one server or across your cluster—just use the Switch Server dropdown in the WebUI.
Tip: While cPFence includes a built-in list of known Tor exit nodes, the Tor network changes frequently. For improved accuracy, you can import an updated list from a trusted external source:
cpfence --bulk-blacklist-ip https://www.dan.me.uk/torlist/?exitTo keep it current, add a daily cron job:
0 3 * * * /opt/cpfence/app/setup/cpfmain --bulk-blacklist-ip https://www.dan.me.uk/torlist/?exitThis ensures your IPDB & WAF always blocks the latest active Tor IPs.
Need Further Assistance?
If you encounter any issues or need additional help, feel free to reach out to our support team via your client portal.

