If you need to exclude specific files, directories, or patterns from being scanned by cPFence, you can use the built-in commands to whitelist them. This can be helpful for trusted files or folders that should not be flagged during virus scans.
Using the WebUI
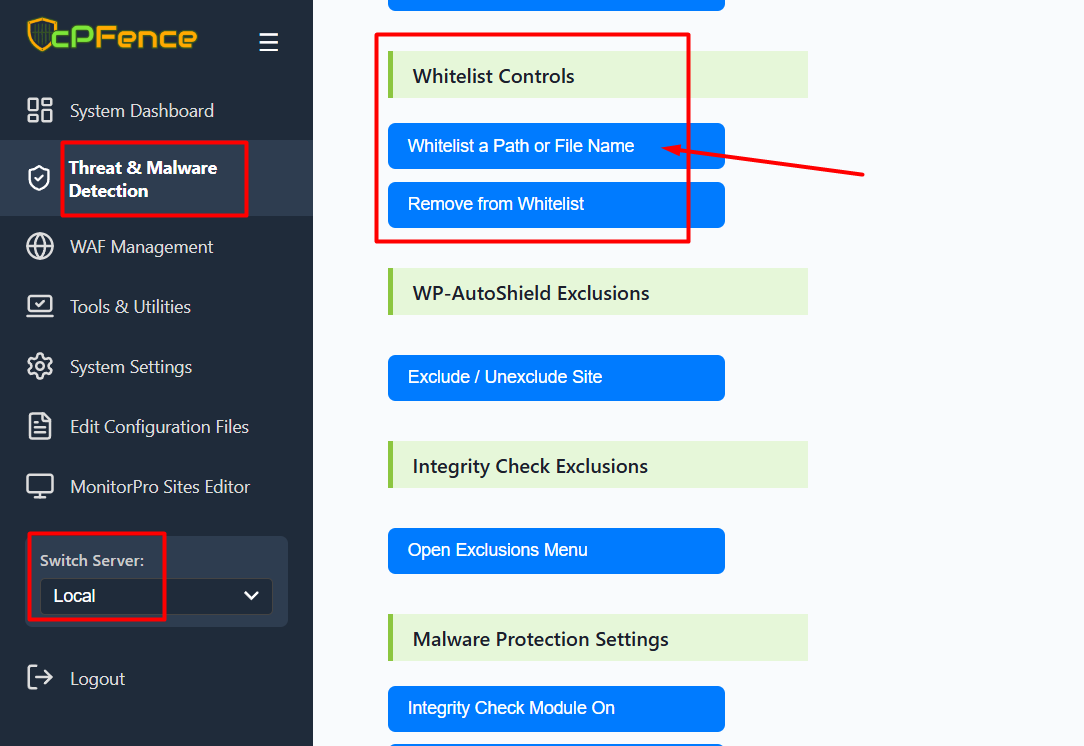
- Go to Threat & Malware Detection in the left sidebar.
- For excluding files or paths, scroll to Whitelist Controls
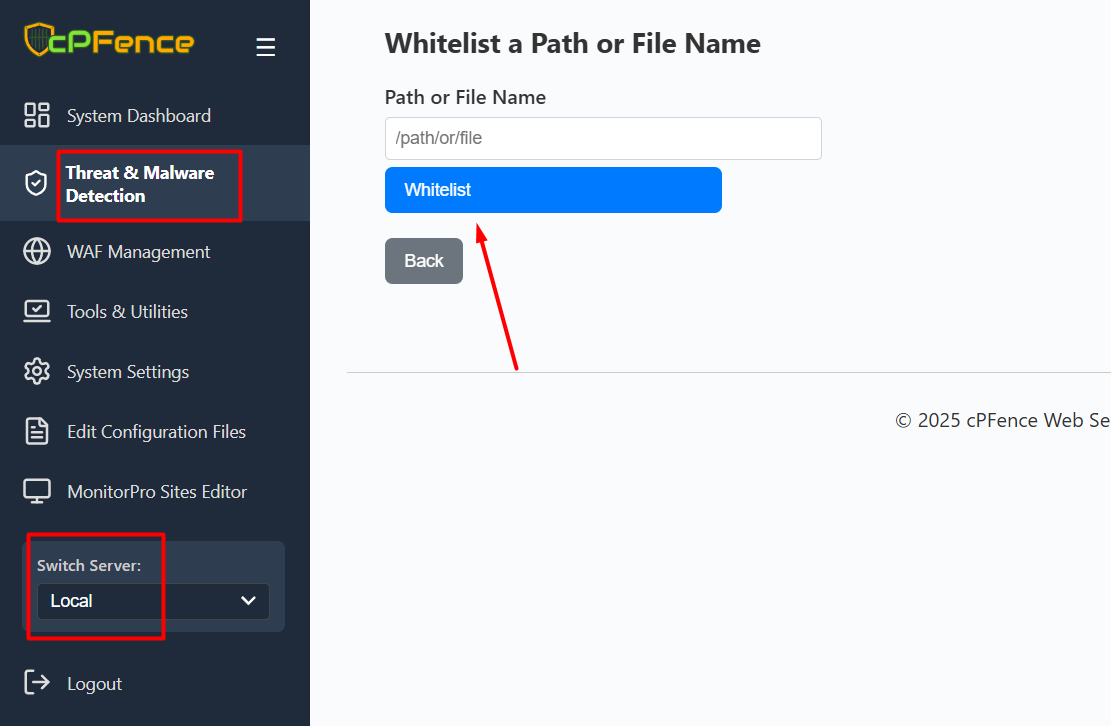
- Click Whitelist a Path or File Name. Enter the path and click Whitelist.
Using the CLI :
Steps to Whitelist Files or Paths
-
1. Whitelist All Files with a Specific Name:
cpfence --exclude-path /error_logThis command will whitelist all files named error_log across your sites. It’s useful if the file appears in multiple directories but is trusted.
-
2. Whitelist a Specific File:
cpfence --exclude-path /var/www/example.com/wp-content/uploads/image.jpgThis command will whitelist only the specified file (e.g.,
image.jpg) in the specified path. This is ideal for singular trusted files. -
3. Whitelist a Path and Its Subdirectories:
cpfence --exclude-path /var/www/example.com/wp-content/uploads/This command will whitelist the
uploadsdirectory and all its subdirectories and files. Useful for trusted directories like media libraries. -
4. Whitelist Any Path Containing a Substring:
cpfence --exclude-path /wp-content/This command will whitelist any path containing
/wp-content/, which could match files across multiple installations.
Advanced Exclusions
-
5. Whitelist a File by Hash:
cpfence --exclude-hash /path/to/your/file.txtExclude a specific file’s hash from scanning jobs. Useful for trusted but flagged files.
-
6. Remove a File Hash from Whitelist:
cpfence --del-exclude-hash HASHRemove a specific hash from the whitelist if it’s no longer needed. Example:
cpfence --del-exclude-hash d41d8cd98f00b204e9800998ecf8427e -
7. Whitelist a Virus Signature:
cpfence --exclude-sig SIGNATURE_NAMEExclude a specific signature from most virus scanning jobs. Example :
cpfence --exclude-sig Heuristics.Phishing.Email.SpoofedDomain -
8. Remove a Virus Signature from Whitelist:
cpfence --del-exclude-sig SIGNATURE_NAMERemove a previously whitelisted signature if it’s no longer needed.
When to Whitelist Files or Folders?
Consider whitelisting paths only when necessary, such as:
- Trusted Custom Scripts: Files that are essential to your application but might be flagged due to uncommon behavior.
- Backup Folders: Exclude folders containing backups to avoid unnecessary scans.
- Temporary Files: Exclude directories with auto-generated temporary files that are frequently changing.
Whitelisting should only be used for paths that you trust completely. Adding unverified paths may compromise your server's security.
Need Further Assistance?
If you encounter any issues or need help, please contact our support team via the client portal.

