To manually test the WAF (Web Application Firewall) on your site, you can use the cPFence WAF Testing Tool, available at cPFence WAF Test, is a simple tool designed to help you verify if your cPFence Web Application Firewall (WAF) is active and functioning correctly.
Steps to Use the Tool:
-
Access the Tool:
- Go to cPFence WAF Test.
-
Enter Your Website URL:
- Input the URL of the website where you've deployed cPFence WAF.
-
Run the Test:
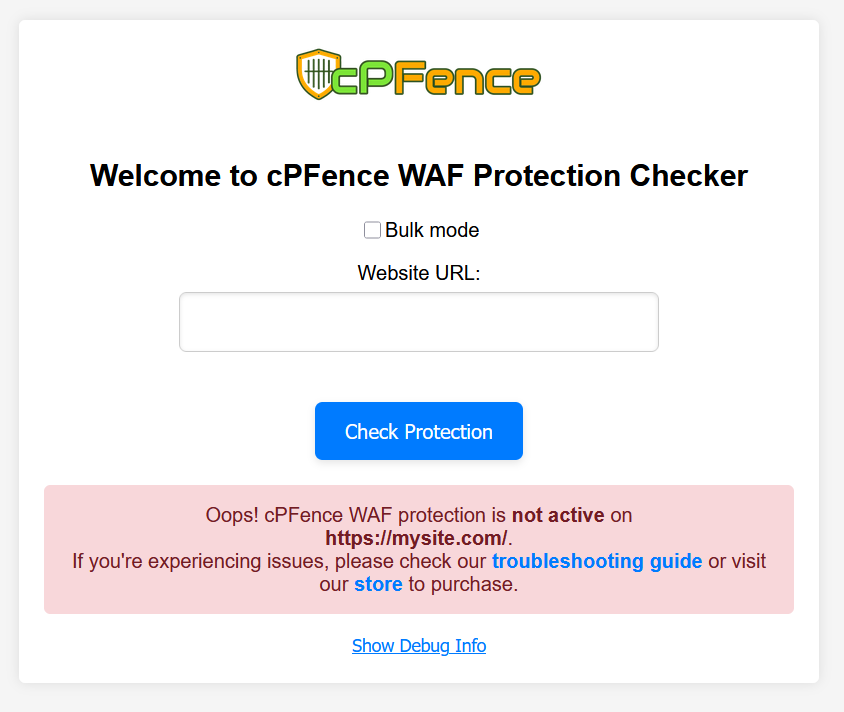
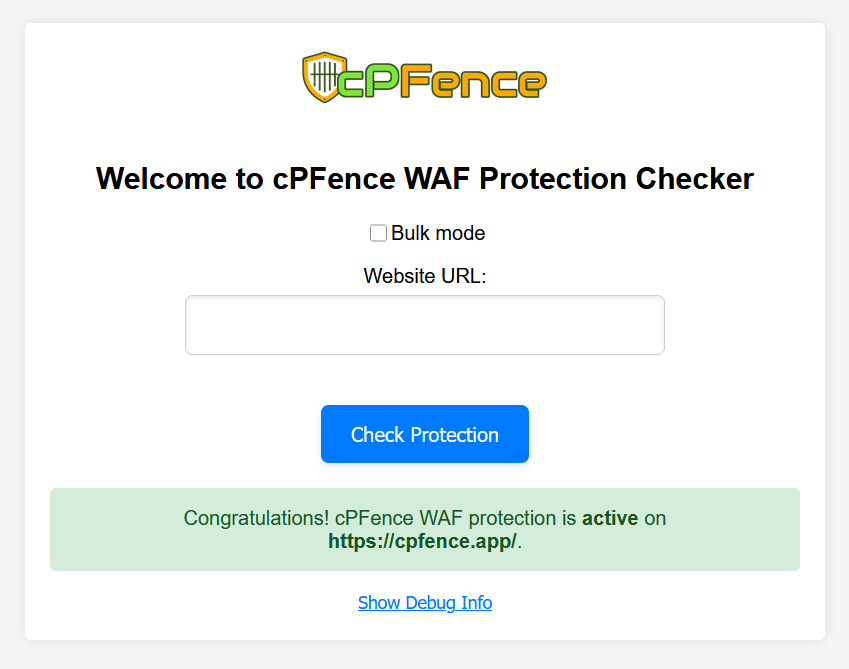
- Click on the “Check Protection” button. The tool will quickly check if the WAF is active on your site.
-
Check the Results:
- The tool will display a message indicating whether the cPFence WAF is active or inactive on your site.
Read also : WAF Not Working? Learn How to Troubleshoot
Using this tool is an easy way to ensure that your cPFence WAF is properly installed and protecting your web application. If you need further help don't hesitate to contact support team.

